Cybercrime is an ever-growing concern in the digital age, with hackers becoming increasingly sophisticated in their attacks. From stealing personal information to conducting ransomware attacks, cybercrime can have devastating consequences for both individuals and organizations. In this blog, we will take a closer look at some of the most common cybercrime attacks being carried out by hackers today.
Phishing attacks
Phishing attacks are one of the most common types of cybercrime, and they involve sending fake emails that look like they come from a reputable source, such as a bank or online retailer. These emails typically contain a link to a fake website where users are prompted to enter their login details or personal information. Once the user has entered their information, the hacker can use it to access their accounts or steal their identity.
Phishing attacks are one of the most prevalent forms of cybercrime, and they are becoming increasingly sophisticated. These attacks can target individuals or businesses and can result in significant financial losses or the theft of sensitive information. Phishing attacks typically involve sending an email that appears to come from a trusted source, such as a bank or social media site. The email will contain a link to a fake website that looks identical to the legitimate site, and users are prompted to enter their login credentials or personal information. The attacker can then use this information to gain access to the user’s accounts or steal their identity.

Phishing attacks can also take the form of smishing (SMS phishing), vishing (voice phishing), or even spear-phishing, where the attacker targets a specific individual or organization. These attacks can be highly targeted and can involve extensive research to create a convincing message. To protect against phishing attacks, it is essential to be vigilant and to follow best practices for online security. Here are some tips to help you avoid falling victim to a phishing attack:
- Check the sender’s email address: Be wary of emails that come from unfamiliar or suspicious email addresses. Always check the sender’s email address to ensure that it is legitimate.
- Look for spelling and grammar errors: Phishing emails often contain spelling and grammar errors, as they are often written by non-native English speakers.
- Verify links before clicking: Always hover your cursor over links in emails to check the URL before clicking. If the link looks suspicious, do not click on it.
- Use two-factor authentication: Two-factor authentication can add an extra layer of security to your accounts, making it more difficult for attackers to gain access.
- Stay informed: Stay up-to-date with the latest phishing trends and techniques to stay one step ahead of attackers.
In conclusion, phishing attacks are a serious threat to online security, and it is essential to take steps to protect yourself from these attacks. By following best practices and staying vigilant, you can help to prevent phishing attacks and safeguard your personal information
Ransomware attacks
Ransomware attacks involve hackers infecting a computer or network with malware that encrypts the data on the system, making it inaccessible to the owner. The hacker then demands a ransom payment in exchange for the decryption key needed to unlock the data. These attacks can be devastating for businesses, as they can result in significant financial losses and damage to reputation. Ransomware attacks are a growing concern for businesses and individuals alike. These attacks involve infecting a computer or network with malware that encrypts the data on the system, making it inaccessible to the owner. The attacker then demands a ransom payment in exchange for the decryption key needed to unlock the data.
Ransomware attacks can be carried out in a variety of ways, including through phishing emails or by exploiting vulnerabilities in software or systems. Once the malware has infected the system, it will typically begin encrypting files and data, rendering them useless to the owner. The attacker will then display a message demanding payment in exchange for the decryption key needed to unlock the data.

Ransomware attacks can have significant financial and operational consequences for businesses. Not only can they result in lost revenue, but they can also damage a company’s reputation and erode customer trust. Furthermore, paying the ransom does not guarantee that the data will be restored, and it may even encourage further attacks. To protect against ransomware attacks, it is essential to implement robust cybersecurity measures. Here are some best practices to help protect your organization from ransomware attacks:
- Regularly backup data: Regular backups can help to minimize the impact of a ransomware attack by allowing you to restore data from a backup if necessary.
- Implement software updates: Ensuring that all software is up-to-date can help to prevent ransomware attacks by patching vulnerabilities that attackers may exploit.
- Train employees: Training employees on how to recognize and avoid phishing emails and other social engineering tactics can help to prevent attacks.
- Use antivirus software: Antivirus software can help to detect and prevent malware from infecting your system.
- Develop an incident response plan: Having a plan in place to respond to a ransomware attack can help to minimize the damage and facilitate a speedy recovery.
In conclusion, ransomware attacks can have serious consequences for businesses, and it is essential to take steps to protect against these attacks. By implementing robust cybersecurity measures and staying vigilant, you can help to prevent ransomware attacks and protect your organization’s data.
Malware attacks
Malware is a type of software that is designed to cause harm to a computer system. This can include viruses, worms, and Trojan horses, which are all designed to either steal data or cause damage to the system. Malware attacks can be difficult to detect and can cause significant damage if left unchecked.
Malware attacks are a common form of cybercrime that involve infecting a computer or network with malicious software designed to cause harm or steal sensitive information. Malware can take many different forms, including viruses, trojans, and spyware. Malware attacks can have significant consequences, including data theft, system corruption, and financial losses. Malware can be distributed through a variety of channels, including email attachments, malicious websites, and software downloads.

To protect against malware attacks, it is essential to implement robust cybersecurity measures. Here are some best practices to help protect your organization from malware attacks:
- Use antivirus software: Antivirus software can help to detect and prevent malware from infecting your system.
- Keep software up-to-date: Ensuring that all software is up-to-date can help to prevent malware attacks by patching vulnerabilities that attackers may exploit.
- Train employees: Training employees on how to recognize and avoid phishing emails and other social engineering tactics can help to prevent malware attacks.
- Use firewalls: Firewalls can help to block unauthorized access to your network and prevent malware from spreading.
- Implement access controls: Limiting user access to sensitive data and systems can help to prevent malware attacks by reducing the number of potential targets.
In addition to these best practices, it is also essential to stay informed about the latest malware threats and to regularly review and update your cybersecurity policies and procedures. In conclusion, malware attacks are a serious threat to online security, and it is essential to take steps to protect yourself and your organization from these attacks. By implementing best practices and staying vigilant, you can help to prevent malware attacks and safeguard your data and systems.
DDoS attacks
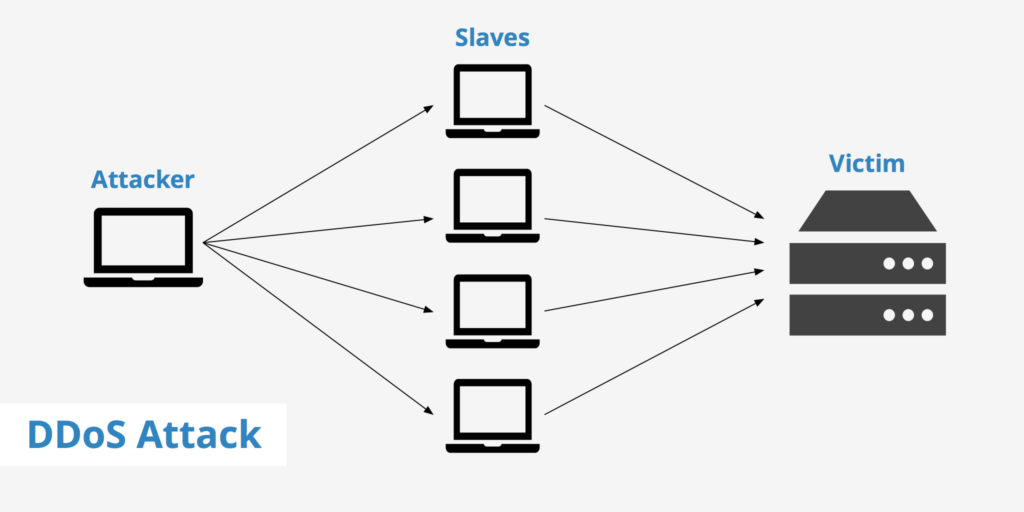
Distributed denial-of-service (DDoS) attacks are designed to overwhelm a website or network with traffic, causing it to become inaccessible to users. These attacks are typically carried out by a network of computers that have been infected with malware and can cause significant disruption to businesses and organizations. A Distributed Denial of Service (DDoS) attack is a type of cyber attack that involves overwhelming a website or network with traffic, making it inaccessible to users. DDoS attacks can be carried out using a network of compromised computers or devices, known as a botnet, which are controlled by the attacker.
DDoS attacks can have significant consequences for businesses, including lost revenue, damage to reputation, and reduced customer trust. DDoS attacks can also be used as a smokescreen to distract from other cyber attacks, such as data theft. To protect against DDoS attacks, it is essential to implement robust cybersecurity measures. Here are some best practices to help protect your organization from DDoS attacks:
- Use a Content Delivery Network (CDN): A CDN can help to distribute traffic across multiple servers, reducing the impact of a DDoS attack.
- Implement network security measures: Network security measures, such as firewalls and intrusion prevention systems, can help to detect and prevent DDoS attacks.
- Use DDoS protection services: DDoS protection services can provide additional protection against DDoS attacks by filtering traffic and blocking malicious requests.
- Keep software up-to-date: Ensuring that all software is up-to-date can help to prevent DDoS attacks by patching vulnerabilities that attackers may exploit.
- Develop an incident response plan: Having a plan in place to respond to a DDoS attack can help to minimize the impact and facilitate a speedy recovery.
In addition to these best practices, it is also essential to stay informed about the latest DDoS attack trends and to regularly review and update your cybersecurity policies and procedures. In conclusion, DDoS attacks are a serious threat to online security, and it is essential to take steps to protect yourself and your organization from these attacks. By implementing best practices and staying vigilant, you can help to prevent DDoS attacks and ensure the availability of your website or network.
Social engineering attacks
Social engineering attacks are a form of cyber attack that relies on human psychology and trust to manipulate individuals into divulging sensitive information or performing actions that can compromise the security of an organization. Social engineering attacks can take many forms, including phishing emails, pretexting, baiting, and tailgating. Phishing emails, for example, are designed to trick individuals into clicking on a malicious link or providing sensitive information, such as login credentials or financial data.
Pretexting involves creating a false scenario to gain access to sensitive information, such as pretending to be a vendor or supplier. Baiting involves leaving an enticing item, such as a USB drive, in a public place, hoping someone will pick it up and use it, thus compromising their computer. Tailgating involves following someone into a restricted area by pretending to be an authorized person. To protect against social engineering attacks, it is essential to implement robust cybersecurity measures and educate employees on how to recognize and avoid these attacks. Here are some best practices to help protect your organization from social engineering attacks:

- Train employees: Training employees on how to recognize and avoid social engineering attacks can help to prevent these attacks from being successful.
- Use multi-factor authentication: Multi-factor authentication can help to prevent unauthorized access to sensitive information by requiring additional authentication steps.
- Implement access controls: Limiting user access to sensitive data and systems can help to prevent social engineering attacks by reducing the number of potential targets.
- Develop an incident response plan: Having a plan in place to respond to social engineering attacks can help to minimize the impact and facilitate a speedy recovery.
- Use security awareness training: Regular security awareness training can help to keep employees informed about the latest social engineering tactics and how to avoid them.
In addition to these best practices, it is also essential to stay informed about the latest social engineering attack trends and to regularly review and update your cybersecurity policies and procedures. In conclusion, social engineering attacks are a serious threat to online security, and it is essential to take steps to protect yourself and your organization from these attacks. By implementing best practices and staying vigilant, you can help to prevent social engineering attacks and safeguard your data and systems.
Instagram and Facebook are two of the most popular social media platforms, with millions of users sharing their personal information and photos every day. Unfortunately, these platforms are also a prime target for hackers looking to steal user information or gain unauthorized access to accounts. One common method of hacking Instagram and Facebook accounts is through phishing scams. Hackers may create fake login pages or send phishing emails that appear to be from Instagram or Facebook, tricking users into entering their login credentials. Once the hacker has access to the user’s login information, they can take control of the account, change the password, and lock the user out.
Another common method of hacking Instagram and Facebook accounts is through brute force attacks. This involves using software to try a large number of password combinations until the correct one is found. This method is often used in combination with social engineering tactics, such as obtaining personal information about the user through their social media profiles or online activity. To protect against Instagram and Facebook hacking, it is essential to take proactive steps to secure your accounts. Here are some best practices to help protect your accounts:
- Use strong passwords: Using strong passwords that include a combination of letters, numbers, and symbols can make it more difficult for hackers to gain access to your accounts.
- Enable two-factor authentication: Two-factor authentication adds an extra layer of security by requiring a second verification step, such as a text message or code generator.
- Be wary of phishing scams: Be cautious of emails or messages that ask you to log in or provide personal information, especially if they are unsolicited.
- Keep software up-to-date: Ensuring that all software, including browsers and social media apps, is up-to-date can help to prevent vulnerabilities that attackers may exploit.
- Monitor your accounts: Regularly monitoring your accounts for suspicious activity, such as unauthorized logins or changes to your profile, can help you to detect potential hacking attempts early.
In conclusion, Instagram and Facebook hacking are serious threats to online security, and it is essential to take steps to protect your accounts. By implementing best practices and staying vigilant, you can help to prevent hacking attempts and safeguard your personal information.
Discover more from Sporty Vaibhav
Subscribe to get the latest posts sent to your email.


